In this Top 5 Wifi Hacking Tools we will be talking about a very
popular subject: hacking wireless networks and how to prevent it from
being hacked. Wifi is often a vulnerable side of the network when it
comes to hacking because WiFi signals can be picked up everywhere and by
anyone. Also a lot of routers contain vulnerabilities which can be
easily exploited with the right equipment and software such as the tools
included with Kali Linux. A lot of router manufacturers and ISPs still
turn on WPS by default on their routers which makes wireless security
and penetration testing even more important. With the following Top 5 Wifi Hacking Tools you are able to test our own wireless networks for
potential security issues. For most tools we’ve supplied a link to a
tutorial which will help you get started with the tools. Let’s start off
the Top 5 Wifi Hacking Tools with the first tool:
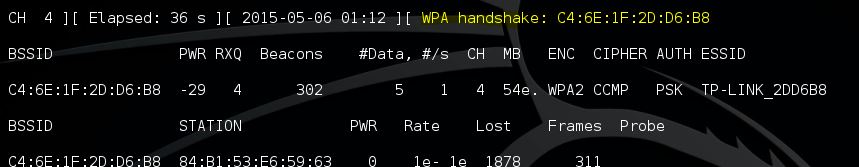
– Aircrack-ng for wireless password cracking
– Aireplay-ng to generate traffic and client de-authentication
– Airodump-ng for packet capturing
– Airbase-ng to configure fake access points
The Aicrack-ng suite is available for Linux and comes standard with Kali Linux. If you plan to use this tool you have to make sure your Wifi card is capable of packet injection.
Website: https://www.aircrack-ng.org/
Tutorial: https://www.hackingtutorials.org/wifi-hacking/how-to-hack-upc-wireless-networks/
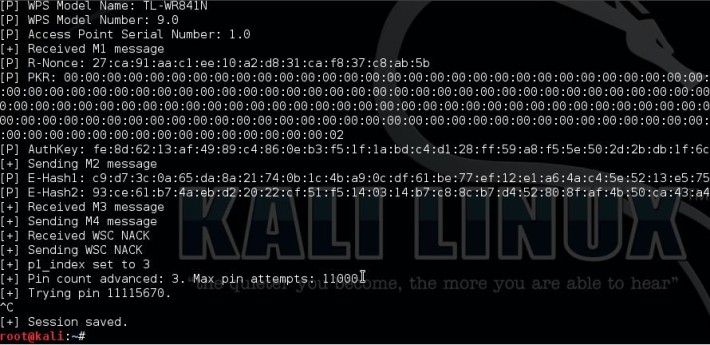
Number 2 in the Top 5 Wifi Hacking Tools is Reaver. Reaver is another popular tool for hacking wireless networks and targets specifically WPS vulnerabilities. Reaver performs brute force attacks against Wifi Protected Setup (WPS) registrar PINs to recover the WPA/WPA2 passphrase. Since many router manufacturers and ISPs turn on WPS by default a lot of routers are vulnerable to this attack out of the box.
In order to use Reaver you need a good signal strength to the wireless router together with the right configuration. On average Reaver can recover the passphrase from vulnerable routers in 4-10 hours, depending on the access point, signal strength and the PIN itself off course. Statistically you have a 50% chance of cracking the WPS PIN in half of the time.
Website: https://code.google.com/p/reaver-wps/
Tutorial: https://www.hackingtutorials.org/wifi-hacking/pixie-dust-attack-wps-in-kali-linux-with-reaver/
Website: https://github.com/wiire/pixiewps/
Modified Reaver: https://github.com/t6x/reaver-wps-fork-t6x
Tutorial: https://www.hackingtutorials.org/wifi-hacking/pixie-dust-attack-wps-in-kali-linux-with-reaver/
Wifite is an automated tool to attack multiple wireless networks encrypted with WEP/WPA/WPA2 and WPS. On start-up Wifite requires a few parameters to work with and Wifite will do all the hard work. It will capture WPA handshakes, automatically de-authenticate connected clients, spoof your MAC address and safe the cracked passwords.
Website: https://code.google.com/p/wifite/
Wireshark is included with Kali Linux but also available for Windows and Mac. For certain features you do need a Wifi adapter which is supports promiscuous and monitoring mode.
Website: https://www.wireshark.org
Tutorial: https://www.howtogeek.com/104278/how-to-use-wireshark-to-capture-filter-and-inspect-packets/
Or follow one of these online courses:
– Wireshark Crash Course
– Wireshark Tutorial – Get Wireshark Certification
1 Aircrack-ng
Aircrack is one of the most popular tools for WEP/WPA/WPA2 cracking. The Aircrack-ng suite contains tools to capture packets and handshakes, de-authenticate connected clients and generate traffic and tools to perform brute force and dictionary attacks. Aicrack-ng is an all-in-one suite containing the following tools (among others):– Aircrack-ng for wireless password cracking
– Aireplay-ng to generate traffic and client de-authentication
– Airodump-ng for packet capturing
– Airbase-ng to configure fake access points
The Aicrack-ng suite is available for Linux and comes standard with Kali Linux. If you plan to use this tool you have to make sure your Wifi card is capable of packet injection.

Website: https://www.aircrack-ng.org/
Tutorial: https://www.hackingtutorials.org/wifi-hacking/how-to-hack-upc-wireless-networks/
2 Reaver
Number 2 in the Top 5 Wifi Hacking Tools is Reaver. Reaver is another popular tool for hacking wireless networks and targets specifically WPS vulnerabilities. Reaver performs brute force attacks against Wifi Protected Setup (WPS) registrar PINs to recover the WPA/WPA2 passphrase. Since many router manufacturers and ISPs turn on WPS by default a lot of routers are vulnerable to this attack out of the box.
In order to use Reaver you need a good signal strength to the wireless router together with the right configuration. On average Reaver can recover the passphrase from vulnerable routers in 4-10 hours, depending on the access point, signal strength and the PIN itself off course. Statistically you have a 50% chance of cracking the WPS PIN in half of the time.

Website: https://code.google.com/p/reaver-wps/
Tutorial: https://www.hackingtutorials.org/wifi-hacking/pixie-dust-attack-wps-in-kali-linux-with-reaver/
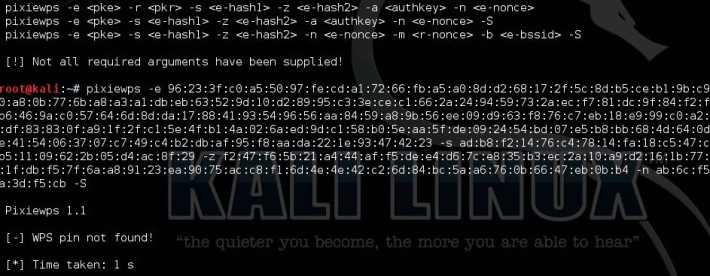
3 Pixiewps
PixieWPS is a relatively new tool included with Kali Linux and also targets a WPS vulnerability. PixieWPS is written in C and is used to brute force the WPS PIN offline exploiting the low or non-existing entropy of vulnerable access points. This is called a pixie dust attack. PixieWPS requires a modified version of Reaver or Wifite to work with. Since this tools has become quite popular in little time, it earns the number 3 in our Top 5 Wifi Hacking Tools list.

Website: https://github.com/wiire/pixiewps/
Modified Reaver: https://github.com/t6x/reaver-wps-fork-t6x
Tutorial: https://www.hackingtutorials.org/wifi-hacking/pixie-dust-attack-wps-in-kali-linux-with-reaver/
4 Wifite
Wifite is an automated tool to attack multiple wireless networks encrypted with WEP/WPA/WPA2 and WPS. On start-up Wifite requires a few parameters to work with and Wifite will do all the hard work. It will capture WPA handshakes, automatically de-authenticate connected clients, spoof your MAC address and safe the cracked passwords.
Website: https://code.google.com/p/wifite/
5 Wireshark
Wireshark is one of the best network protocal analyzer tools available, if not the best. With Wireshark you can analyse a network to the greatest detail to see what’s happening. Wireshark can be used for live packet capturing, deep inspection of hundreds of protocols, browse and filter packets and is multiplatform.Wireshark is included with Kali Linux but also available for Windows and Mac. For certain features you do need a Wifi adapter which is supports promiscuous and monitoring mode.
Website: https://www.wireshark.org
Tutorial: https://www.howtogeek.com/104278/how-to-use-wireshark-to-capture-filter-and-inspect-packets/
Or follow one of these online courses:
– Wireshark Crash Course
– Wireshark Tutorial – Get Wireshark Certification
So for more queries you can comment us below..
And you can also join us on Instagram and Facebook






















